Leveraging AI for Effective Threat Hunting and Detections

Many of us have been there: the daily threat feeds, threat exchange platforms, combing through lists of IOCs of varying difficult formats, even sometimes manually keying in from screenshots. All of this just to gather data to write threat hunting queries and detection rules. With AI, we can make our lives a little bit easier when it comes to basic hunting and detection, and even learn a few things in the process.
Background#
First things first, if you haven’t heard of Sigma or RootA - you are missing out!
To put things simply:
SigmaandRootAare open-source projects that focus heavily on community contributions and rule sharing for the means of threat hunting and threat detection.- Both
RootAandSigmaaim to improve the efficiency and effectiveness of threat detection through innovative query languages and approaches. RootAacts as an open-source wrapper on top of existing SIEM, EDR, XDR, and Data Lake query languages, while Sigma is a specific query language for detection algorithms.
Essentially, we can leverage the interoperability of these languages to target our existing platforms using AI tools like Uncoder.io or alternatively, an open source tool Sigconverter.io. Bonus points for hosting local models with Ollama, maximizing data security (more on this in the future).
Usage and Examples#
For example, if I have a Sigma rule for detecting exploitation of CVE-2024-37085, I can use that rule to provide me with a query in Kusto Query Language (KQL) if I use Microsoft Sentinel or Defender for Endpoint. The same can be done for Splunk (SPL), SentinelOne, Carbon Black, or whatever other platform you use in your environment. We can then build detections or simply run ad-hoc queries.
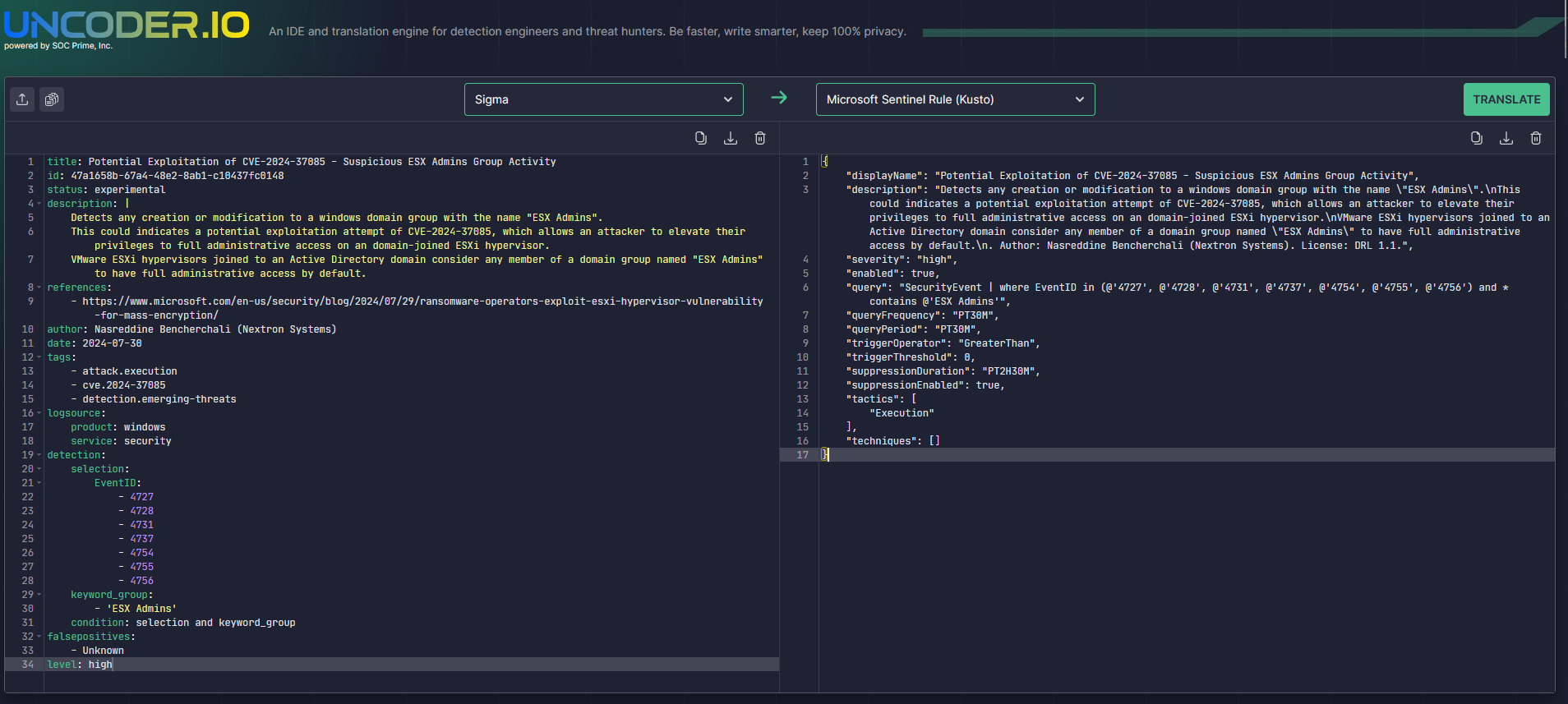
Sigma Rule to Microsoft Sentinel Analytics Rule#
To demonstrate, I will take the experimental Sigma rule for detecting exploitation of CVE-2024-37085 and put it in the input side of Uncoder. For the output, I will use Microsoft Sentinel Rule (Kusto) as an example. Once I press translate, we get an output almost instantly and can put this to use with Analytics rules in Azure Sentinel.
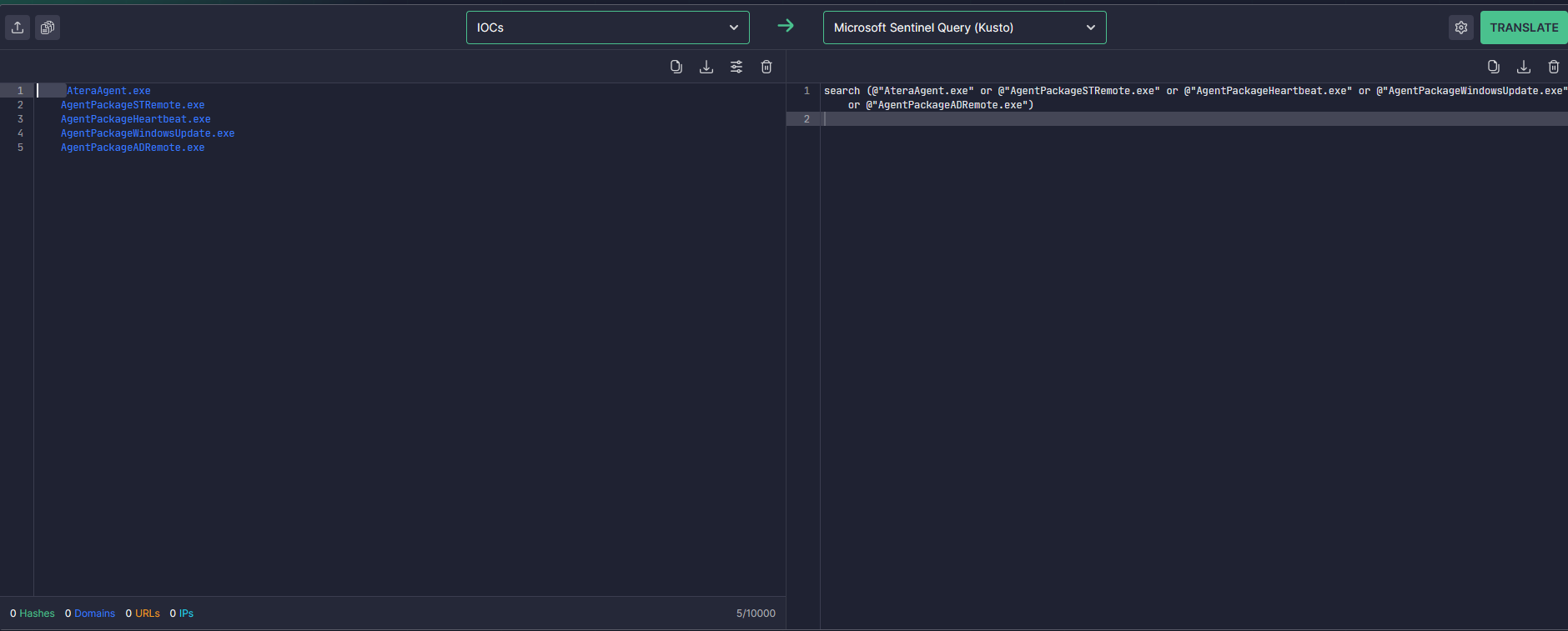
IOCs to Microsoft Sentinel Kusto (KQL) Query#
As I eluded to earlier, you can also input bare IOCs instead of Sigma or RootA rules. Your input can include common junk identifiers and formatting and it will get rid of anything that is irrelevant or not file hashes, process names, or IP addresses, for example.
In the below example, you can see I have extra whitespace before my process names that is removed when I generate the query.
Disclaimer: I want to mention that you should not use these tools as a crutch, and if you do not understand what we are looking to accomplish when building query logic - you may end up missing what you intended to hunt for. As with AI tools, your mileage may vary and I recommend tweaking the output to your environment as everyone’s event schema is different!
Closing#
As threat hunting and detection continue to evolve, it will be interesting to see how these AI-powered tools and query languages shape the way we approach detections. Whether you’re a seasoned SOC warrior or just starting out, understanding the capabilities and limitations of these tools is essential for effective threat hunting and detection in today’s complex security landscape.