Attacking CUPS: A ‘Half-Empty’ RCE Vulnerability?

Summary#
Security researcher, Simone Margaritelli, otherwise known as @evilsocket, has disclosed a vulnerability in OpenPrinting CUPS, an open source printing system for GNU/Linux systems.
This vulnerability is currently assigned 4 CVEs at the time of writing, all of which are reserved by a CNA (CERT).
- CVE-2024-47176
- CVE-2024-47076
- CVE-2024-47175
- CVE-2024-47177
The vulnerability allows an attacker to perform an unauthenticated remote code execution attack against systems running CUPS. Earlier, there was speculation from Simone that engineers from RedHat and Canonical have evaluated a CVSS:3.1 score of 9.9, but this is still to be determined and the general consensus in online discussions is that the vulnerability is overblown, but new information is still coming to light. The full scope of impact has been rumored to affect all GNU/Linux systems, including macOS as mentioned by Simone himself, and does not have an official patch at this time. Please treat the information in this article as preliminary due to the nature of the disclosure.
This disclosure comes after Margaritelli attempted to follow responsible disclosure procedures with the OpenPrinting development team and was met with resistance and frustration after presenting multiple proof-of-concepts, and discussions spanning over 100 pages. In the interest of persuading the developers to push a patch out quickly, Margaritelli had decided to disclose the vulnerability early due to apparent leaks in CERT’s Vulnerability Information and Coordination Environment (VINCE), ahead of the scheduled early October disclosure. In my opinion, this was the most interesting part of following this story - you can read more about the process from Simone here.
Visible Global Impact#
For some perspective, a quick Shodan search query shows over 90,000 CUPS web interfaces exposed to the public internet:
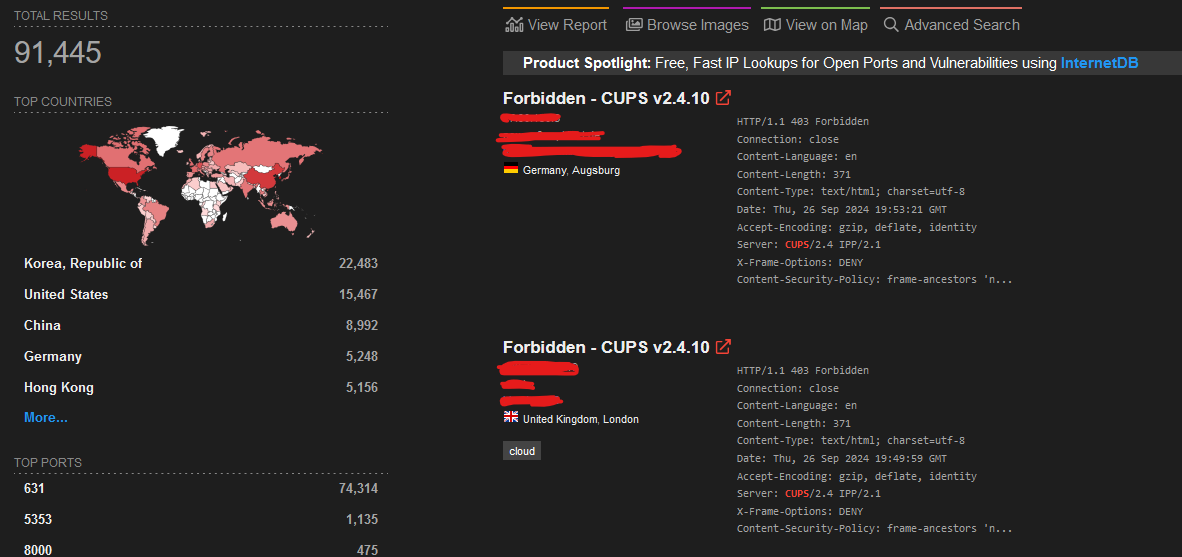 It will be interesting to see how this number changes over the next few days.
It will be interesting to see how this number changes over the next few days.
The rest of this post will consist of summarized information (tailored for the blue teams responding to this disclosure) from Simone’s post on the matter.
Impact and Affected Systems:#
Margaritelli has been scanning the public internet to put together a list of current versions of Linux that are impacted. That list spans over 2300 lines and can be found here. One may assume with a reasonable degree of certainty that their UNIX systems are in scope. It does vary whether CUPS is enabled by default or not on your system.
When exploited, an attacker can replace and install new printers’ IPP URLs with malicious ones to execute commands remotely once a print job starts. The kicker here is that this attack can be done without any authentication and the first entry point is to send a UDP packet to port 631, this is assigned to CVE-2024-47176, a flaw in versions of cups-browsed equal to or earlier than 2.0.1. It is also important to note that a print job will need to be triggered for remote commands to be executed after the attack is staged. I’m sure we will see some creative exploits in the next few days, Margaritelli also mentioned implementing his exploit into Bettercap.
The following remediation/mitigation advice was provided by Simone Margaritelli:
Mitigation#
Remediation
- Disable and remove the
cups-browsedservice if you don’t need it (and probably you don’t).- Update the CUPS package on your systems.
- In case your system can’t be updated and for some reason you rely on this service, block all traffic to UDP port 631 and possibly all DNS-SD traffic (good luck if you use zeroconf).
Entirely personal recommendation, take it or leave it: I’ve seen and attacked enough of this codebase to remove any CUPS service, binary and library from any of my systems and never again use a UNIX system to print. I’m also removing every zeroconf / avahi / bonjour listener. You might consider doing the same.
Note: This post is early summary coverage of the disclosure and information is subject to change without notice as things develop.